Getting My Webintegrity To Work
Wiki Article
Not known Details About Webintegrity
Table of ContentsThe smart Trick of Webintegrity That Nobody is DiscussingGet This Report about WebintegrityThe Main Principles Of Webintegrity

If you run an e-commerce service, you'll want
to optimize your servers to avoid issues like downtime, bandwidth overload and long loading times. website alerts. Monitoring your network in real time can reveal workable understandings regarding glitches and efficiency inadequacies that require to be resolved."Not just do service leaders get to know the status of their network efficiency and also protection at all times, however when an event happens, the real-time alerting permits for faster case reaction, "said Pieter Van, Iperen, owner and taking care of companion of PWV Consultants.
Webintegrity Can Be Fun For Anyone
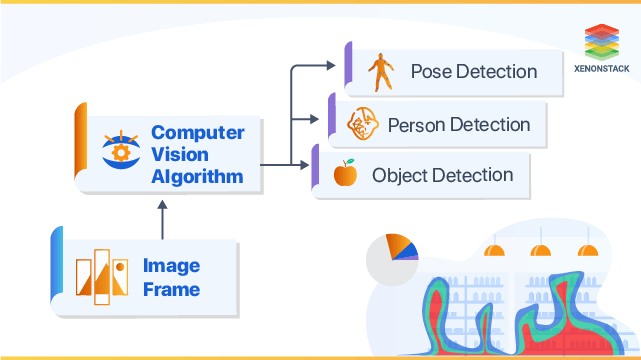
It is very important for companies to resolve events as soon as they develop, nevertheless large or tiny they appear to be." When performance modifications or there is a security alert, the system can inform you to ensure that fixes can be carried out. This is why it is crucial to understand what is typical for the company without understanding what is normal, magnate have no suggestion just how to establish informs (https://s.id/1Dst4)."There are a number of monitoring applications on the market, which range in features, technological competence and price."I advise picking a service that is very easy to apply and make use of. If you need a lot more complex tools in the future, you can update. There is a device to fit every scenario.". By checking functional tasks such as inventory levels or product use patterns, it comes to be simpler for supervisors at any level to recognize which processes demand renovation or optimization.
You can conserve time and resources by executing brand-new ones without initial monitoring if those renovations will actually result in price financial savings over time. Due to the nature of the BAM, managers can react to these exceptions proactively as they can use real-time info. Cflow's BAM can be made use of to observe all your process-relevant tasks that take place throughout your organization (https://webintegrity.jimdosite.com/). You can incorporate activity information and also commute metrics and implement organization rules to set limits for very easy visualization of the kept an eye on data.
Business Refine Measurement(BPM )is a means to keep an eye on as well as gauge business processes, which can be made use of for: Measuring the performance of a process or procedure improvement. Automating service processes. A thing instance is a service things that has actually been instantiated in your system. It represents the smallest system of organization procedure monitoring, which can be made use of to monitor private circumstances of a thing by utilizing its unique identifier (ID). Using just one KPI may not precisely mirror real state of either procedure. Utilizing several KPI metrics assists make sure that administration has access to appropriate info at all times throughout their daily operations. A crucial efficiency sign( KPI )is a dimension of progression toward the accomplishment of a specific objective. One of the most usual kinds of KPIs consist of: Income targets Roi( ROI) metrics Profit margin percentages Metricsare a means to determine and keep track of the efficiency of a business. Metrics specify to business and should be specified prior to starting any kind of BAM job. It is necessary that metrics be defined by the organization individuals, not IT or advertising professionals. g., when an e-mail was sent efficiently yet there was no recipient address kept for that person,this would create the trigger to terminate off an alert concerning "no recipients". A debug log is created after each occasion has occurred. This helps you know what took place during that time period without requiring any added info from customers who logged right into their accounts during those minutes. Without the description debug log, it will become tough to bring back the shed information and to monitor the modifications that took place between the occasions.
Report this wiki page